Underrated Ideas Of Tips About How To Stop Dos Attack

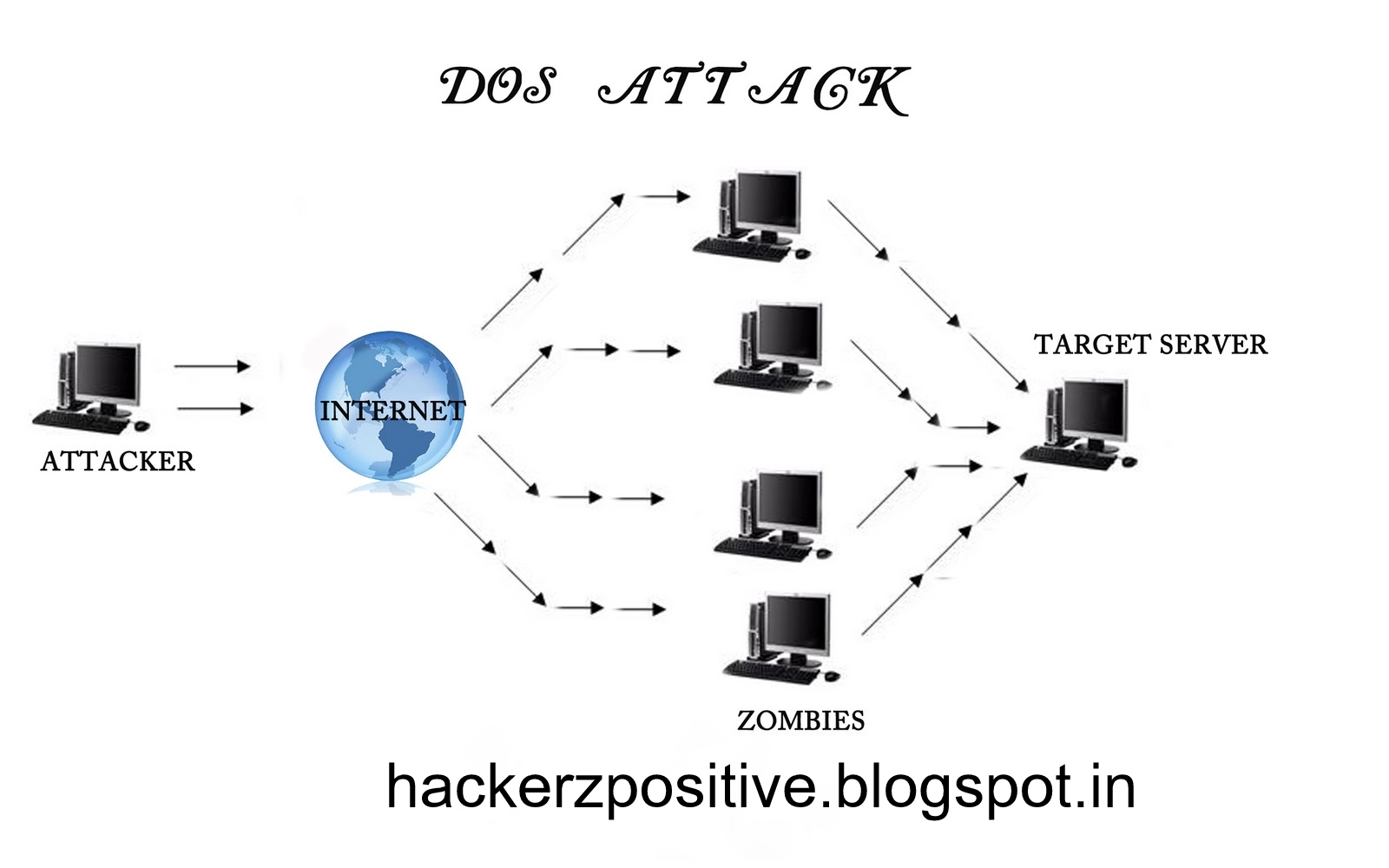
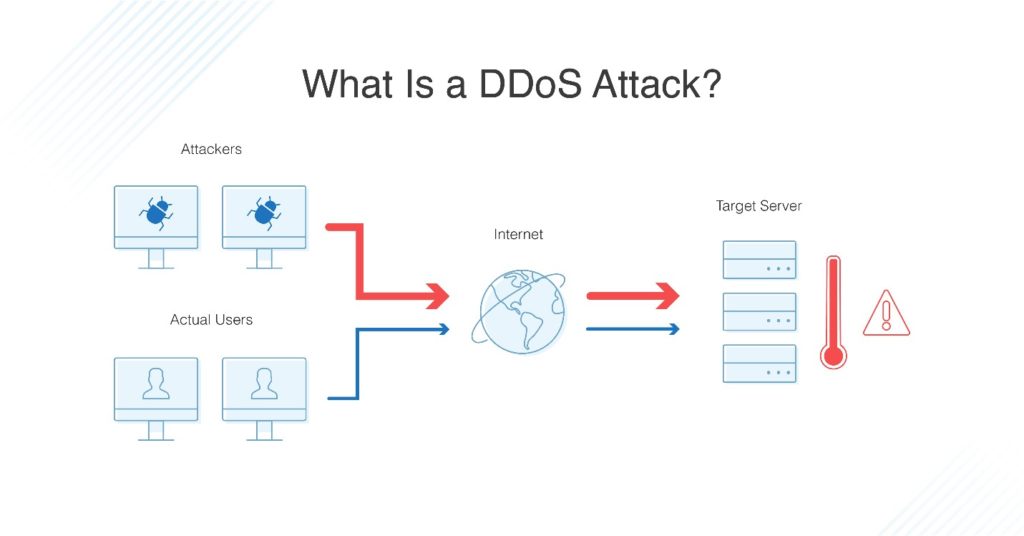
First, dos attacks only use one internet connection to overwhelm a targeted network or website.
How to stop dos attack. March 15, 2022 a “denial of service” or dos attack is used to tie up a website’s resources so that users who need to access the site cannot do so. July 2022 awareness series itsap.80.100 alternate format: Use zombie networks to flood targeted.
Ingress filtering, for example, is a valuable technique for preventing dos attacks. Fix a visual bug in the dragon palace scenery. Prevent single point of failure:
Houthi fighters march during a rally of support for palestinians in the gaza strip and against the u.s. You can’t prevent being a victim of the dos attack. A truly proactive ddos threat defense hinges on several key factors:
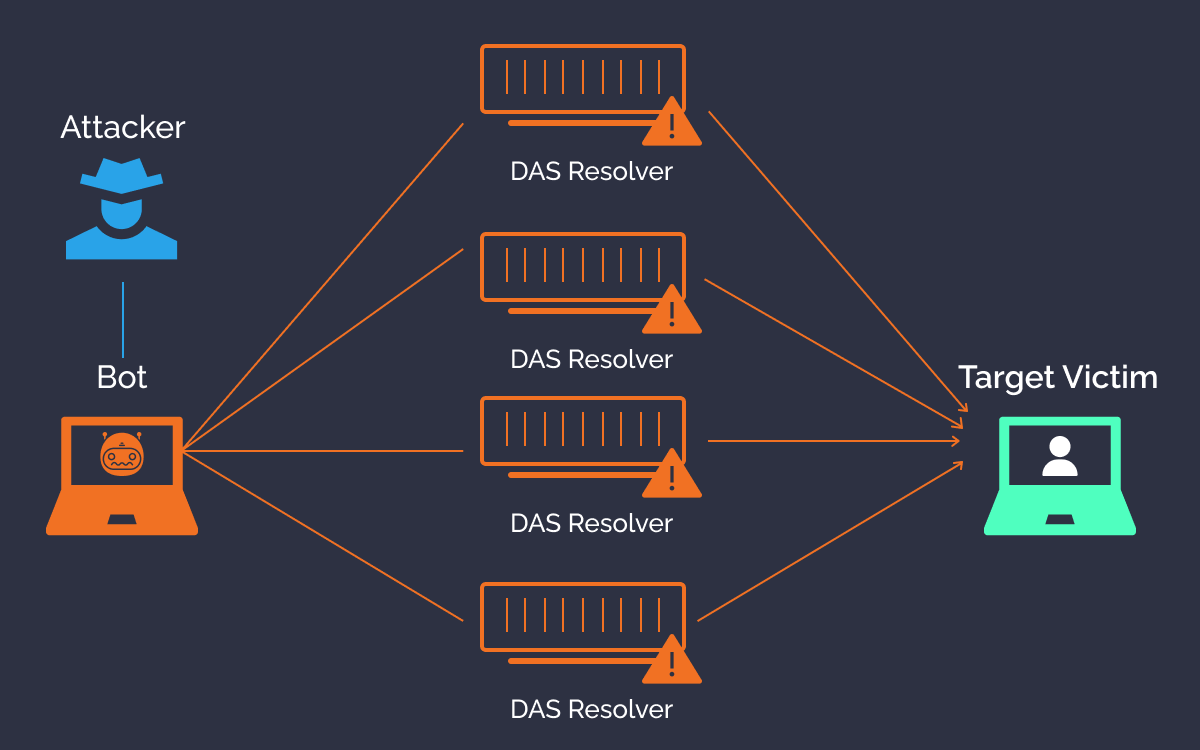
China is mostly quiet on houthi attacks in the red sea. This effectively makes it impossible to stop the attack simply by blocking a single ip address; A common oversight related to preventing dos attacks is a lack of formal, documented incident response plans.
This will cause failure on physical assets, which may, in turn, produce an effect similar to ddos attacks: Target larger networks to affect more users. Distributing network resources across multiple locations isn't just about avoiding a single failure point.
The ping of death takes advantage of this and sends data packets above the maximum limit (65,536 bytes) that tcp/ip allows. Ddos is stopping the attack by either upstream service provider defenses or ddos protections in your local datacenter. There are not many effective ways to that.
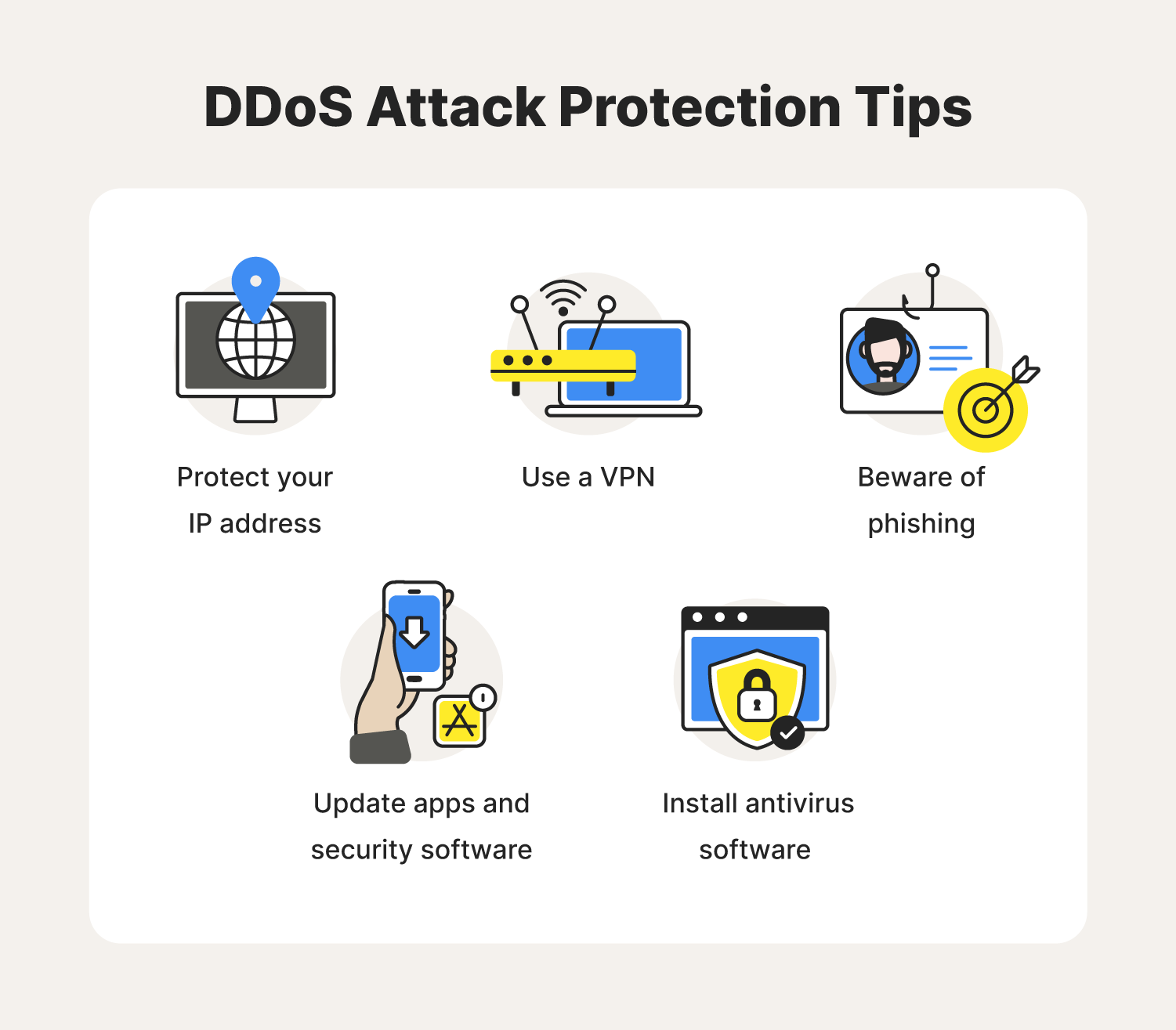
December 2, 2021 | by andreja velimirovic home / security strategy / how to prevent ddos attacks: Preventing a dos attack can be challenging, but there are several effective techniques: Dive in below for the full details of what’s.
Ping of death the ping command is usually used to test the availability of a network resource. Detecting and preventing single points of failure (spof) is key to resisting dos attacks. Sadly, these attacks are becoming more frequent and brutal.
Take immediate steps to attempt to block the attack, which may. Know your network’s traffic. One minute you can be minding your business online and then next you’re being hit by a mountain of traffic that puts you back to the stone age.
Attack surface reduction, threat monitoring, and scalable ddos mitigation tools. In case of a distributed denial of service (ddos) attack, and the. Layer 1 is not a target for ddos attacks but can be a target of physical manipulation, obstruction, or even destruction.










![[dos attack rst scan] How to Change](https://arzhost.com/blogs/wp-content/uploads/2021/11/error.jpg)