Perfect Tips About How To Handle Denial Of Service
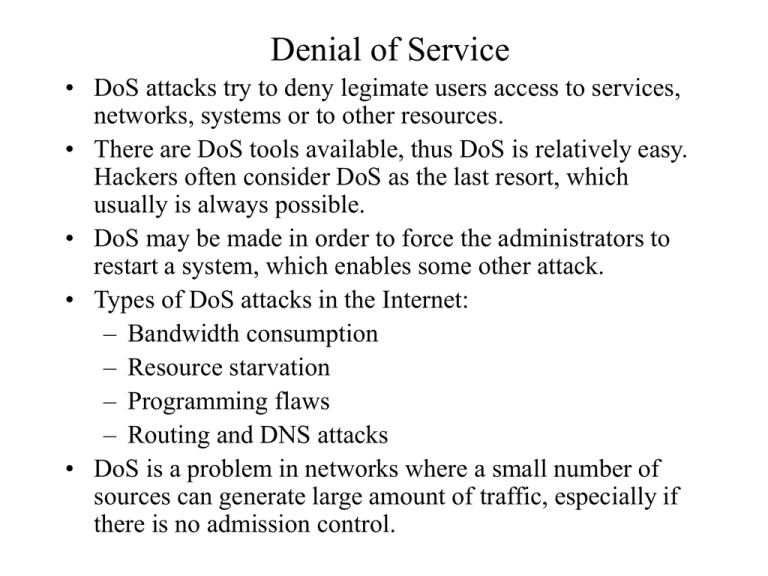
Denial of service can be accomplished in a variety of ways, including programming or logical vulnerabilities, improper handling of resources, or by flooding the targeted.
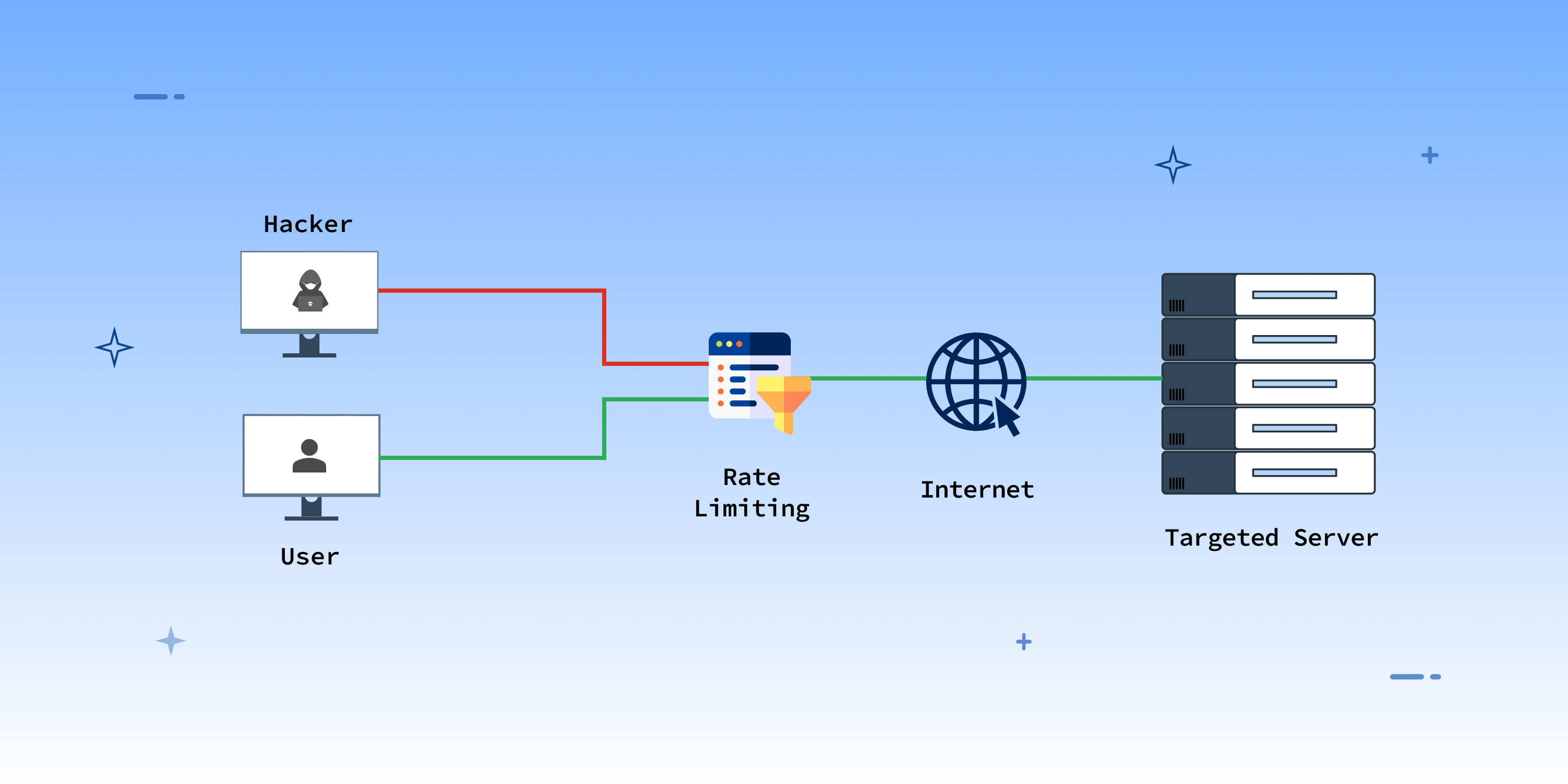
How to handle denial of service. Prevention given that denial of service (dos) attacks are becoming more frequent, it is a good time to review the basics and how we can fight back. These are technical dos attacks and social engineering dos attacks. A denial of service (dos) attack is a malicious attempt to affect the availability of a targeted system, such as a website or application, to legitimate end users.
When under siege from a distributed denial of service (ddos) attack, systems grind to a halt and often become entirely unresponsive. Stopping users from accessing a resource, whether it's a web page, email, the. Dos attacks accomplish this by flooding the.
To stop the attack, defenders. A denial of service (dos) attack is a type of cyberattack that aims to make a computer or network resource unavailable to its intended users. Denial of service attacks come in many forms, but share a common purpose:
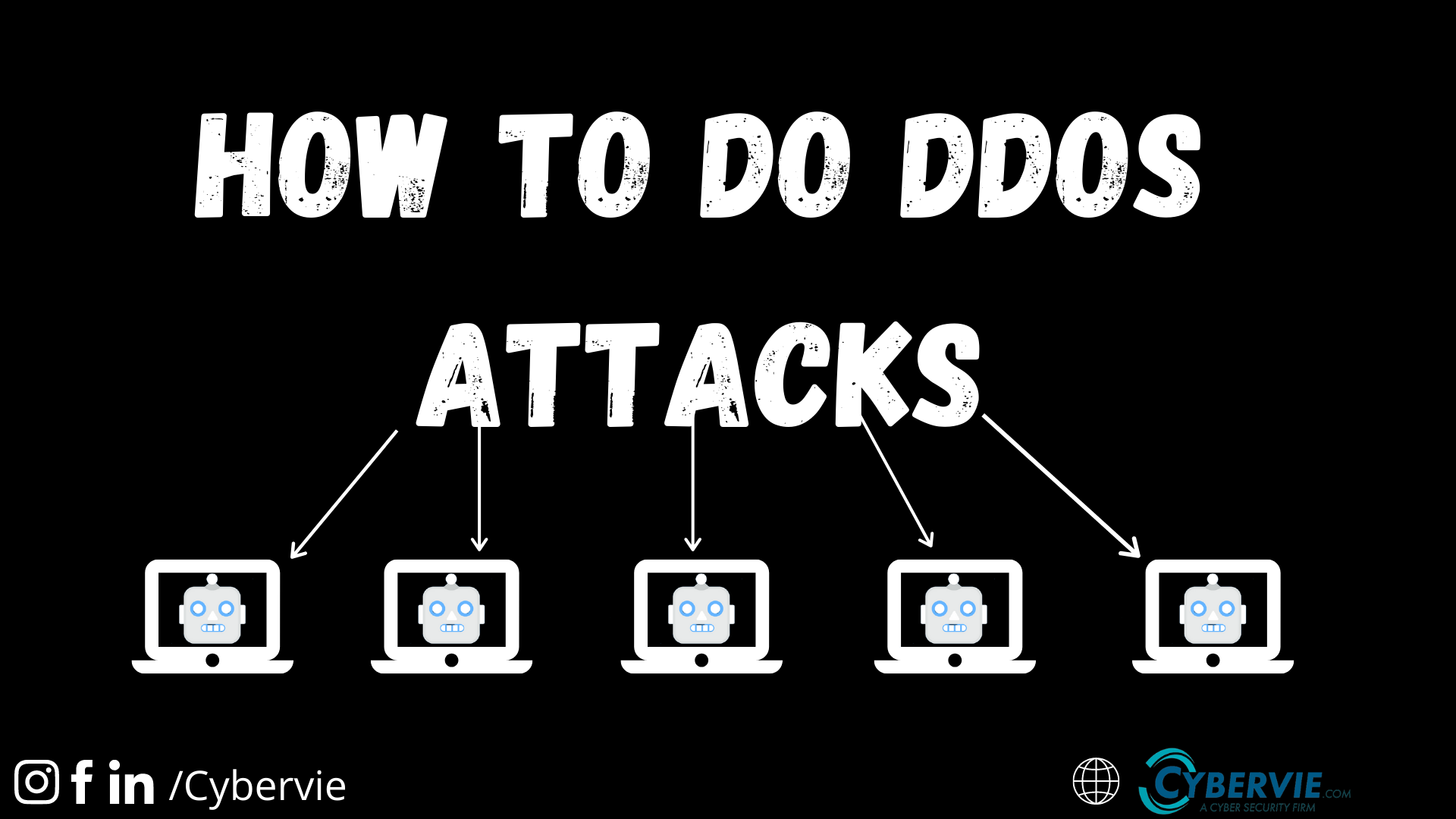
Denial of service (meaning) can be classified into two main categories. What is a ddos attack? Denial of service (dos) attacks aim to flood the victim servers with fake requests, thus preventing them from serving legitimate users.
There are many ways to. Description the denial of service (dos) attack is focused on making a resource (site, application, server) unavailable for the purpose it was designed. Typically, attackers generate large volumes of packets or requests ultimately.
It is usually caused by. Consider if those offered by your provider may be a good fit. When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s ip address, potentially causing the server or network to become overwhelmed,.
The attacks have hit many major.